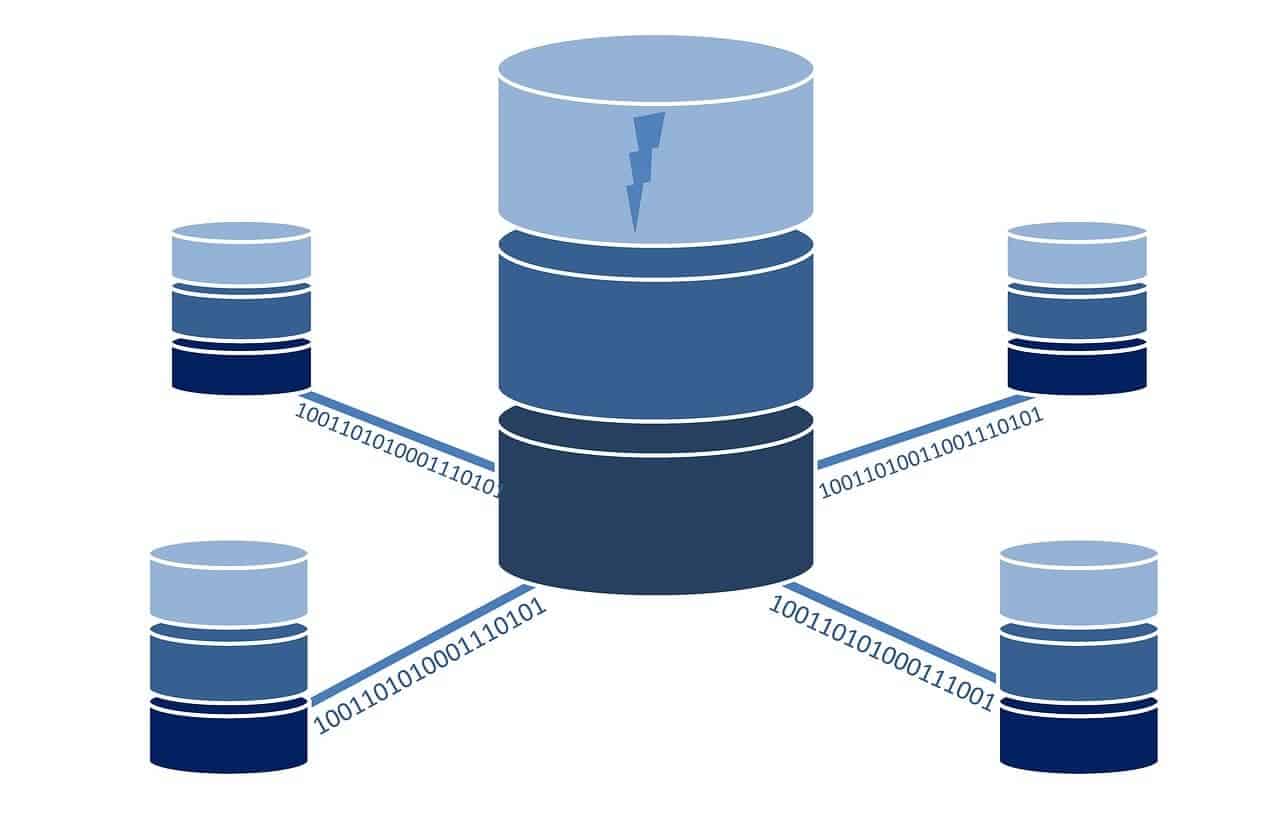
Database administration (DBA) is crucial in designing, developing, and maintaining an organization’s databases. It involves ensuring that data is secure, reliable, and accessible to users when needed.
This article provides an overview of how DBA works by discussing its purpose, components, techniques for optimizing performance, and security measures implemented.
DBA aims to ensure that the database performs at peak efficiency while maintaining optimum levels of accessibility and integrity.
By understanding the basics of DBA workflows, organizations can confidently manage their databases. With this knowledge comes the ability to make decisions that will help ensure organizational success through improved system performance.
What Is Database Administration?
Database Administration (DBA) is a specialized field of information technology that focuses on efficiently managing and maintaining databases. It requires expertise in query optimization, schema design, and other related activities to ensure maximum performance and reliability.
A DBA’s job is to ensure data can be retrieved quickly and accurately while maintaining overall system security. They are responsible for configuring database systems, setting up user accounts, monitoring performance, and making necessary updates or modifications.
DBAs must also test data integrity to verify accuracy and troubleshoot potential issues with existing databases. By doing all this work, a DBA ensures that an organization can access timely and accurate data when needed.
This ability allows organizations to focus on their core business operations without worrying about their data infrastructure. Moving forward, we will discuss the design and development aspects of Database Administration in more detail.
Design And Development:
Database administrators (DBA) are responsible for designing, developing, and maintaining the data architecture of an organization’s databases. This includes scaling architecture to meet the needs of ever-changing business requirements. DBAs also ensure that the database system is highly available, secure, reliable, and always performs optimally.
The DBA role involves creating various structures within a database – such as tables, views, indexes, users, and permissions – to store and organize data efficiently. They must deeply understand relational database design principles, SQL language syntax, and structure query optimization techniques. Additionally, they manage backup processes to keep disaster recovery plans up-to-date and monitor performance metrics regularly.
To develop robust data architectures:
- A DBA should be familiar with normalization rules and best practices for database design.
- Monitor how applications interact with the database to identify and address any issues quickly.
- Follow industry standards when configuring security settings to protect against external threats or unauthorized access.
By following these guidelines, DBAs can build effective data architectures that scale efficiently over time while ensuring high-performance levels throughout their entire lifecycle.
With this knowledge, organizations can trust their systems will remain reliable no matter what changes arise in the future.
Performance Optimization:
As a Database Administrator, performance optimization is essential to ensure smooth and efficient operations. Query tuning is one of the main methods used to optimize database performance. That involves analyzing query execution plans for different types of queries and making adjustments to improve their efficiency.
Additionally, indexing optimization can speed up data retrieval from tables by creating indexes on specific fields. Creating optimal indexes requires understanding how the underlying data structures work and which columns are most often queried against.
Database Security is another vital area that needs attention when managing databases. Proper security protocols must be implemented to protect sensitive information stored within the system from potential threats such as malicious attacks or unauthorized access. It also involves ensuring that user accounts have appropriate permission levels set only to have access to the relevant resources they require while minimizing risk exposure.
With proper security measures, organizations can rest assured knowing their data is safe and secure. Transitioning now into discussing database security…
Database Security:
Database authentication is the process of verifying the identity of users when they attempt to access a database. It typically involves verifying a username and password combination or using biometric or multi-factor authentication methods.
Database encryption is the process of encoding data in a database to prevent unauthorized users from accessing the data. Encryption keys are used to encode and decode the data, making it difficult for attackers to gain access.
Database auditing is tracking and logging activities on a database, such as user logins, data updates, and queries. It allows the dba to monitor user activity and detect unauthorized access attempts.
Database Authentication:
Database authentication is a critical component of database security. A dba must ensure that only authorized users have access to the data stored in the database, and encrypting sensitive data can help mitigate unauthorized access.
Data encryption offers an additional layer of protection by making it harder for hackers to access a user’s account or view confidential information. Access control measures are also crucial as they restrict who can use certain functions within the system, such as creating tables or changing existing records.
These measures are essential in ensuring all users comply with regulatory requirements when working with sensitive data. To further protect against potential breaches, dbas should establish audit trails to monitor changes made over time and quickly identify suspicious activities.
By taking these steps, dbas can give their organization peace of mind knowing that its data is secure from malicious actors looking to exploit weaknesses within systems.
Database Encryption:
Database encryption is critical to database security and enables organizations to protect sensitive data from malicious actors. Encryption strategies can vary depending on the protected information type, with more robust algorithms typically used for more confidential data.
Data encryption also provides an additional layer of protection by making it difficult for hackers to access user accounts or view private information.
To further secure databases, dbas should assess which types of encryption best suit the organization’s needs while adhering to any regulatory requirements that may be in place. This assessment process allows them to create an effective strategy to keep their system safe and ensure users remain compliant when handling confidential data.
Database Auditing:
In addition to encryption, database auditing is another essential component of an effective security strategy.
Database auditing can help dbas understand how their data is being used and identify any potential risks or vulnerabilities in the system.
Through this process, they can ensure that all user accounts are secure and compliant with regulations.
Data warehousing also plays a role in this process by allowing organizations to store large amounts of data for long-term analysis.
Additionally, disaster planning should be considered when developing robust strategies for protecting databases from malicious actors.
By creating comprehensive backups and regularly testing the system, dbas can prepare for any eventuality and quickly restore operations if needed.
Ultimately, proper auditing helps maintain accountability within the organization while providing additional layers of protection against external threats.
Backup And Recovery:
Backup and Recovery are essential components of the day-to-day operations of a Database Administrator (DBA). The DBA is responsible for ensuring that all data stored within their databases are securely backed up and can be recovered in case of disaster. It includes appropriately planning, designing, testing, maintaining, and implementing backup procedures for an organization’s database systems.
Schema design plays a vital role in the success or failure of any Disaster Recovery plan. A well-designed schema will help reduce downtime if there is a need for Recovery from system failures or other disasters. When designing schemas and implementing backups, the DBA should consider the potential for unanticipated threats. By doing so, they minimize risk while giving their users peace of mind that their data is secure.
Database monitoring goes hand-in-hand with Backup and Recovery, as both are necessary to keep business operations running smoothly. As such, it is critical to have regular checks on performance metrics related to the overall health of the database environment to detect issues before they become significant problems.
Database Monitoring:
Database Monitoring is a crucial element of Database Administration. From cost-effectiveness to scalability issues, monitoring helps ensure the database infrastructure performs optimally and efficiently. It also provides an administrator with valuable information about current system performance levels and any potential problems or errors occurring within the environment.
Regarding monitoring, several different tools are available for administrators to utilize, such as SQL Server Profiler, Performance Monitor, and System Monitor. Each tool lets you view vital data related to your databases, including query activity, CPU usage, memory utilization, and more.
Additionally, these tools can provide notifications in case of unexpected or undesired events like long-running queries or deadlocks, which can help prevent costly downtime due to misconfiguration or server overloads. With these powerful tools, DBAs can quickly identify and address any issues before they become significant problems.
Transitioning into the next section – data migration – we will explore how this process works and what considerations need to be considered when planning a successful data migration strategy.
Data Migration:
Data migration involves transferring data from one type of system to another. Database administrators must often manage this process, particularly when scaling up upgrades and transferring between different types of databases or operating systems.
Data conversion is integral to data migration, ensuring data is transferred accurately within a given timeframe. Any potential errors should be identified and resolved during the conversion process to migrate the data successfully.
Database administrators play a critical role in ensuring successful migrations by providing technical expertise on all aspects related to moving large volumes of data, including writing scripts for automation, monitoring the progress of the migration, and troubleshooting any challenges encountered along the way.
With their knowledge and experience in database management, they can ensure that migrations are carried out efficiently with minimal risk to both users and business operations. As such, DBAs are essential for organizations looking to scale up their technology infrastructure without compromising performance or security.
Transitioning to the next section about database management tools will explore how these professionals can use them to streamline processes and maximize efficiency.
Database Management Tools:
Database administrators (DBAs) are responsible for managing a database system. They work to ensure that data is secure and available while providing query optimization and scalability solutions.
DBAs use powerful software tools to create databases, manage user accounts, configure access rights, back up data, and monitor performance.
Cloud hosting has become an increasingly popular choice for many organizations due to its flexibility and cost savings. Cloud-based databases offer elasticity in scaling resources such as storage or CPU cycles according to demand. It allows organizations to reduce costs by allocating only enough processing power when needed instead of paying for more than necessary at any given time.
As cloud computing continues to evolve, so does the role of the DBA, which must keep up with new technologies, including containerization, virtual machine instances, and big data analytics. With these developments comes the immense opportunity for optimizing both performance and security on a global scale.
There are lots of other tasks should need to performed by DBA. Those are depending on situation and company’s requirements.
Conclusion:
The role of database administration is an essential part of any organization that relies heavily on data. DBAs are responsible for designing and developing databases, optimizing performance, securing data, backing up and recovering it as needed, monitoring usage and activity, and migrating data between different platforms.
Database management tools can also simplify the process by providing automated solutions to many tasks. By combining their technical knowledge with a deep understanding of business operations and requirements, DBAs ensure the accuracy and security of information systems to optimize their effectiveness.
Ultimately, this leads to better decision-making across the entire organization. As organizations become more reliant on technology for daily operations, database administrators will remain essential to ensuring smooth operation and success in the future.